“A Perfect Secret” is a metaphor for knowing something but not being able to describe it because the words necessary to describe it exist outside of standard verbal language. All of us have things that we know, but can’t describe; we all have perfect secrets. What follows is an idea for an authentication system based on this premise. Further research would be necessary to determine the viability of this approach, but conceptually, I’m convinced it would work.
Seeing vs. Knowing
People can see things they do not know. It happens all the time when we learn new information. For example, it is possible to see a new word, but not know what it means.
Described as a solution set:
Assume that the set of all visible information is designated as Visible Information.
Assume that the set of Known Visible Information is a subset of Visible Information.
Visible Information > Known Visible Information
Knowing vs. Being Able to Describe
We can also see things and know them on sight, but not be able to put them into words.
Visible Information > Known Visible Information > Known Visible Information that can be Described
Thinking about these things, I wondered: Could we use Known Visible Information that can’t be Described as means to secure information? If a person could create a code based on visible information known to them but that they were unable to describe, then only that person could use the code. Right?
I started thinking about different things that we know, but can’t describe. I arrived at: Moods, feelings, and emotions. We can recognize these things on a person’s face, but they are very hard to describe in any accurate or granular way using language. So I came up with another solution set:
Your Face = The set of information that people most easily recognize
Memory = The set of information that is part of a one way mapping process (learning)
Emotions, Moods, Feelings = The set of information that is impossible to describe in a granular way
Therefore, the complete solution set is: A picture of your own face, having a memory, of a mood, feeling, or emotion.
A picture created from this solution set would be easy to remember, but impossible to describe. A series of such pictures used as a code would be a perfect secret. It couldn’t be shared because it couldn’t be communicated with words (written or verbal). It could, therefore, be used to authenticate that the person able to unlock the code was the person who created the code.
Here’s how it might work in practical terms:
PATTERN SELECTION
Bob needs a secure password that he will be unable to share. Using a digital camera, his employer takes four pictures of him in front of a white background. Bob is told to pose with the following facial expressions: Happy, Laughing, Angry, Sad.
These four pictures are morphed into a spectrum set of 100 pictures. Each of the primary emotions Bob expressed is in one corner of the spectrum.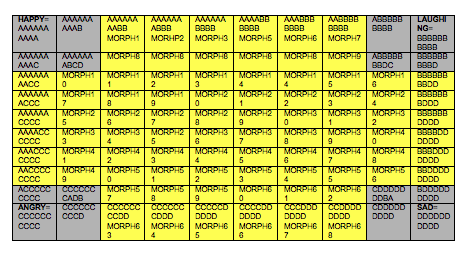
The pictures of the four emotions are thrown out of the set, as are the three pictures closest to each (marked with gray above). Any of these pictures could have been described using the words Happy, Laughing, Angry, Sad. The remaining pictures in the morphed set (marked yellow above) have no accurate verbal descriptions. These keepers are displayed on a touch screen.
Bob is asked if he can differentiate between each of the 84 pictures If he can’t, the spectrum set is reduced. This process is repeated until Bob’s minimum differentiation threshold is crossed. Let’s assume that in the end Bob can tell 20 pictures apart.
PATTERN IMPRINTING:
Bob is asked to select 4 of the 20 pictures as his code. Each of the 4 pictures is flashed several times on the touch screen. Then, the 4 pictures are mixed back with the 16 unselected pictures. All 20 images are then randomly scrambled and re-displayed. Bob attempts to find his four pictures. If he cannot, the training continues until Bob can reliably select the four different variations of his own image.
Bob lacks the language to describe the solution set to anyone. He is unable to “give” anyone his password because it’s impossible to accurately describe a Picture of a Memory of a Mood, Feeling, or Emotion to the level of detail required to share it. Bob could try describing one piece of the code as “sort of happy, a little laughing, but not exactly laughing out loud.” But that is not enough information to enable another viewer to pinpoint the correct image.
This situation would ensure that Bob is actually the person with the authentication code and that Bob is, in fact, Bob.
PATTERN RESOLUTION:
There are many mechanisms that could be employed to resolve the solution set. Here’s the simplest scenario:
Bob enters a secure facility and an enclosed retina-based biometric reader randomly displays his set of 20 images. The screen is configured so that only Bob can see the images. Bob goes down the set visually, row by row, until he identifies the four pictures. The screen is cleared and the four images are displayed. Bob then reorders the pictures in the pattern that matches the solution set.
This approach could also be extended to credit card authentication. When a credit card is swiped, the credit card company could transmit the images to a touch-screen at the transaction location. Bob would select the solution set in a similar manner as above. This information could not be shared. Even if an observer was watching the screen, he or she would not have enough visual information to resolve the differences in the pictures to memorize the “code”. If this was a concern, it would be possible to display the solution set one image at a time, so that comparisons between images would be impossible.
Further, this approach could be applied to secure email communications or any application that requires an authentication mechanism.